First step — Investigation
Investigation 🔎, a.k.a. passive recon (reconnaissance) is the first step of the pentester activities during an external penetration testing.
It involves gathering information about the target from afar 👓️, meaning with no direct interaction with the target(s) 👀.
🌱 The goal is to find as much information as possible.
🚿️ You can also infer data, for instance, if a company has many customers, then they may have a support page/customer service.
📚 This could also mean passively observing the network activity if we are already within the company network.
Common activities:
-
🧑💻 Learn more about the company (roles, services...), the technologies, programming languages and software they use...
-
🐟 Find a potential attack vector (website, provider, etc.)
-
🧑 Find information about their employees, their emails, their social accounts, their leaked passwords...
-
...
OSINT Gathering
Open-source intelligence "OSINT" encompasses any information that we gather from public sources. Refer to the osintframework.com.
Social Networks — LinkedIn OSINT 🧑🐟
You can easily find company employees using LinkedIn.
- ☑️ Are they still claiming to be in the company?
- ✍️ Note down their first name, last Name
- ☎️ Is there an email/phone number in their description?
- 🌍 Did they link a personal blog in their description?
- 🎯 Did they set up some contact emails?
The main problem is that many profiles may not be visible from our account. You can use solutions to access LinkedIn API. For marketing purposes, they are also returning professional and personal emails (if any is known or had leaked). Refer to LinkedIn OSINT Tools.
Email Investigation — Find Accounts 🧑🐟
There are multiple solutions to investigate an email address:
- epieos
[FREEMIUM]: Find accounts details - spokeo
[FREEMIUM]: Find accounts on common websites - holehe
[FREE](7.6k ⭐): Find accounts on common websites - social-analyzer
[FREE](11.6k ⭐): same as holehe - GHunt
[FREE](15.7k ⭐): gmail, groups, drives... - Twint
[FREE](15.8k ⭐, 2021 🪦): Twitter scrapping tool - ProtOSINT
[FREEMIUM](0.3k ⭐, 2021 🪦): Obsolete - Osintgram (8.4k⭐) and Instaloader (8.7k ⭐): Instagram
There are multiple solutions to identify email addresses given a company domain (e.g. example.com). But, such solutions are not always trustworthy. For instance, they may return delete emails or AI-generated emails when the mail server was hardened.
- hunter
[FREEMIUM]: Company emails - Tomba
[FREEMIUM]: Company emails - SkyMEM
[FREEMIUM]: Email lists - EmailSearch
[PAID]: 👻 - Snov
[FREEMIUM]: 👻 - FindEmails
[PAID]: 👻 - OSINT Industries
[PAID]: 👻 - EmailRep
[FREEMIUM]: 👻
📚 Leaks tools supporting domain search can also be used.
Username Investigation — Find Accounts 🧑🐟
Assuming you have identified a username that may have been reused across multiple platforms by the target, you can find which one using:
- Sherlock (59.8k ⭐)
[FREE] - Maigret (10.2k ⭐)
[FREE] - NameCheckup
[FREE] - WhatsMyName (1.7k ⭐)
[PAID]
GitHub Investigation — Find Targets 🧑🐟
Assuming you have identified a GitHub/GitLab organization or a username associated with the company, you can use:
- GitHub: Gitrob 🪦 (5.9k ⭐, dev names, languages, projects...)
- Git: shhgit 🪦 (3.8k ⭐, find secrets)
- Github: GitFive (0.8k ⭐, search by email/username)
Phone Investigation — Find Accounts 🧑🐟
Assuming you have identified a phone number, you can use:
- PhoneInfoga (13.0k ⭐)
[FREE]
Deep/Dark Web — Data Leaks 🧑🐟
Data Leaks includes credentials (username, password, hash), IPs, addresses, and domains. They are the result of a breach or an user being compromised by an infostealer. Given a domain (ex: example.com) or an email (ex: toto@example.com), we can find data leaks using:
| Name | Pricing | API | Uncensored |
|---|---|---|---|
| Aura 👑👑 | [FREE] |
❌ | ❌ |
| BreachDirectory | [FREEMIUM] |
✅ | ❌ |
| DeHashed 👑 | [PAID] |
✅ | ✅ |
| Enzoic | [PAID] |
✅ | ✅ |
| HackCheck 👑👑👑 | [PAID] |
✅ | ✅ |
| LeakBase | [PAID] |
❌ | 👻 |
| LeakCheck 👑👑👑 | [PAID] |
✅ | ✅ |
| LeakedDomains | [PAID] |
✅ | 👻 |
| LeakLookup | [PAID] |
✅ | 👻 |
| LeakPeek | [PAID] |
❌ | ✅ |
| ProxyNova | [FREE] |
❌ | ✅ |
| Snusbase 👑 | [PAID] |
✅ | ✅ |
| WeLeakInfo | [PAID] |
✅ | 👻 |
We can find infostealers and their collected data using:
| Name | Pricing | API | Uncensored |
|---|---|---|---|
| HackedList | [PAID] |
✅ | ??? |
| HudsonRock 👑 | [FREE] |
✅ | ❌ |
| HudsonRock 👑👑 | [PAID] |
✅ | ✅ |
| WhiteIntel | [FREEMIUM] |
✅ | ❌ |
There are costly but powerful platforms to monitor telegram and the dark/deep web:
- Intelligence X (👻)
- SearchLight Cyber (👻)
- DarkAtlas (👻)
- SocRadar (Very limited as a free user)
- Kela Cyber (Only the last 2 years of data, quite good, relatively costly)
- DarkOwl (Too many unparsed breaches, limited capabilities but cheaper)
Additional services:
- Have I Been Pwned
[FREE][API]: lists breaches with a description - Have I Been Pwned
[FREEMIUM]: lists breaches given an email - LeakCheck
[FREE][API]: lists breaches given an email - CyberNews
[FREE]: lists breaches given an email - Mozilla Monitor
[FREE]: finds information on a breach (limited) - DDoSecrets
[FREE]: download data breaches
📚 From infostealers logs, you can identify login portals, username formats per login portal, password policy, etc. Later, you can try brute force a login portal with a few possible passwords.
Discovering Subdomains
By examining DNS records and certificates issued for a domain, we can passively learn about:
- 🗺️ Public domains and subdomains used by the company
- 📮 Mail Server configuration through MX records
- ✍️ Externally connected apps through TXT records
- 🧑 Targets for social engineering attacks
- 🛣️ Servers and IP ranges
- ...
Discovering Hosts — IP Ranges
IP ranges are given by the client during a pentest, but there are some platforms which can be used to access this public information.
- arin (US) and ripe (EU)
- BGP Toolkit, BGP View+API
- netcraft
- VirusTotal
From an IP, you can get the ASN using ipwhois.
Discovering Information — DNS Records + Registrar
You can find social engineering information on non-european websites by investigating the registrar information.
The target may expose things in their DNS records. Aside from during CTFs, we only learn about external solutions from TXT records.
Discovering Subdomains — Certificate Transparency (CT)
Most companies are using an SSL/TLS certificate per domain. Since certificates are public, we can inspect them to find subdomains.
- crt.sh
[FREE]: the most used platform - ctfr (1.9k ⭐, 2020 🪦)
[FREE]: tool to access crt.sh - ct search
[FREE]: include expired certificates - censys
[???]: 👻 - netcraft
[???]: 👻
Most of these have a clear limitation: some companies are using wildcard certificates e.g. *.example.com which hides their subdomains.
Discovering Subdomains — Known Subdomains
Some websites are keeping track of every DNS they found while monitoring and investigating the web.
- VirusTotal
[FREEMIUM]: the best reference - RapidDNS
[FREE]: not useful - SubdomainsFinder
[FREE]: not useful - DNS Dumpster
[FREE]: not useful - Sublist3r
[FREE]: unmaintained - Subfinder
[FREE]: free with some FREEMIUM/PAID APIs
📚 Use them for each wildcard certificate returned using CT.
Discovering Subdomains — Multipurpose tools
A few tools you may use:
- TheHarvester: automate many of the tools listed
- DNSRecon: access CRT, reverse lookup
- knock: shodan + virus total
OneAudit Investigation
From a domain to a complete report about the company external surface using passive recon tools.
We developed oneaudit (0.01k ⭐) to ease and automate the process of external passive recon. It is built over many existing tools.
1. OneAudit Subdomains Investigation
Given a domain such as example.com, we can list its subdomains using: oneaudit automate -d example.com -o .output -vv.
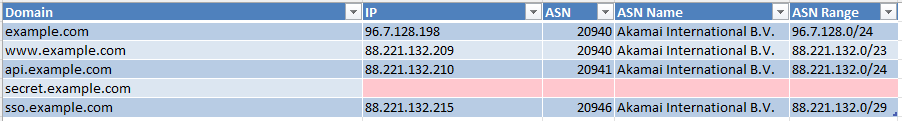
2. OneAudit Hosts Investigation
We want to investigate each IP owned by the target company. Companies can have public hosts not associated with a domain, or not with a domain that we identified. If you identified any interesting IP ranges, add them to the scan. The command is: oneaudit automate -d example.com -o .output -vv -s '<found>,A.B.C.D/24'.
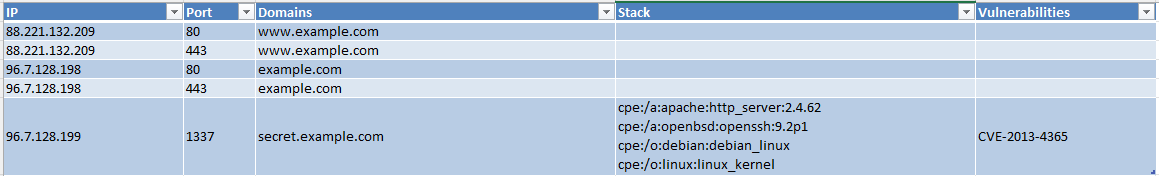
📚 Some company registered have their own IP Ranges. Make sure to check every ASN you found before running the command with -s.
3. OneAudit Employees Investigation
So far, we focused on machines. We now want to investigate every employee that is currently working in the target company. You can do that using: oneaudit automate [...] --format first.last.
Run the command with -vv to confirm if your format seems likely ("verified" means "the mail existed", stats are shown at the end of the logs).
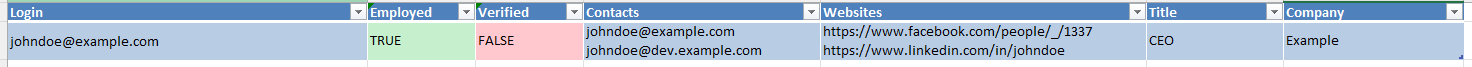
⚠️ If you still cannot guess the format, skip this step for now.
📚 Look for contact forms or Whois/ASN records for emails.
4. OneAudit Leaks Investigation
Finally, we want to find leaked passwords as they may still be used. We may uncover additional emails from old leaks. You can fetch the leaks (with or without a target list) with: oneaudit [...] --qleaks.
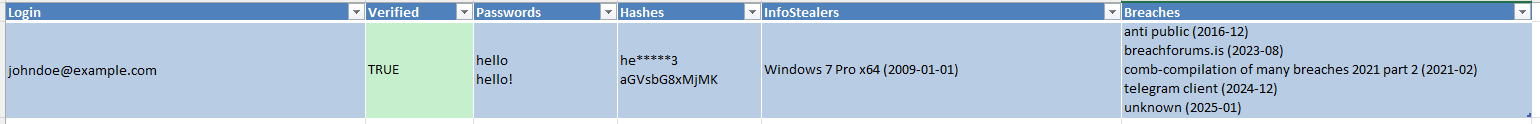
Breach dates are often invalid due to them sometimes surfacing years later to the marketplace, either individually or in a "new" compilation.
👻 To-do 👻
Stuff that I found, but never read/used yet.
- cloud-based services and platforms investigation
- Wireless network reconnaissance
- Google dorking 🧑💻🐟🧑: find anything indexed by google
- Shodan 🐟: find exposed and potentially vulnerable IoT devices
- Maltego 🧑💻 🐟: find websites, domains, social media accounts...
Websites
- Wayback machine 🐟: see previous versions of the website
Internal Assessments
- Passive Network Discovery 🃏: map the internal network

