Networking
A network is a net of devices connected to each other, such as all the devices connected to your internet box 💻.
These devices need to communicate (securely!) between each other ✉️.
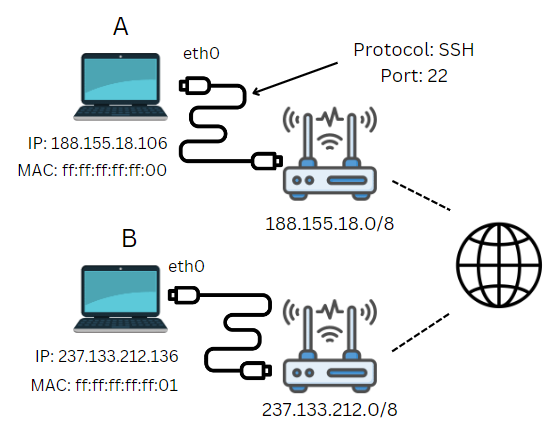
Some elements that are involved, shown in the simplified schema:
-
IP Address 🌍: each network device has an IP address. This allows us to find where a machine is. Example:
188.155.18.0. -
MAC Address 🏠: an IP address is not fixed. If a network device is connected to another network, it will have a new IP address. A MAC address is a unique identifier to identify a device.
-
Network interface 📶: this is the logical representation of the network card used to connect a device to a network. We can have multiple of them. Example:
eth0. -
Protocol 🔐: a format/language for exchanging messages, so that different devices can communicate with each other. Example:
SSH. -
Port 🐊: each protocol uses a specific (logical) channel for messages. For example, if a machine receives a message on port
22, they will expect the protocol to beSSH...
IP Addresses and MAC address
IP addresses 🌍
An IP address is a unique identifier assigned to each device on a network. It's used to locate a device on the network. There are two kind of IP addresses:
There is a shortage of IPV4 since many years, due to the great amount of connected devices, leading to a shift from IPV4 to IPV6.
MAC address 🏠
A media access control address (MAC address) is a unique address set by the network interface vendor.
This is a 6-bytes-long address such as ff:ff:ff:ff:ff:ff with 12 hexadecimal characters, separated by a colon.
- The first 6 characters are identifying the vendor/manufacturer. This is called a OUI (Organizationally unique identifier).
- The last 6 characters are the unique address
Each Network interface has one.
Interfaces and ports
Interfaces
A network interface (NIC)/adapter/card is a physical component connecting your machine and the network. A virtual network interface is the virtual representation of the physical component 📶.
Common (virtual network) interfaces are
eth0,eth1... 🧦: for ethernet adapterstun0,tun1... 🪂: for VPN adapterslo(loopback) 🏡: for the localhost virtual network (127.0.0.1)
The loopback interface is used by local applications to share data between themselves, over the localhost network.
Maximum Transmission Unit (MTU) 🛂: to avoid data loss, each interface has a maximum size for a packet. The default MTU of lo is 65536ko, while for others it is 1500ko. Bigger packets are fragmented.
Ports
A port is a virtual messaging channel which is only associated with one protocol, such as 22 associated with SSH. This association allows a machine to correctly handle a message using the correct protocol.
- 🗃️ There are 65535 (or in short $2^{16}$) available ports
- 🔒 The first 1024 ports are called "well-known/system ports"
- ☘️ Ports 1024 to 49151 are called "registered ports"
- 🍀 Ports 49152 to 65535 are called "dynamic/private ports"
🗺️ List of TCP/UDP ports and their protocols.
- 🤔 A protocol can be re-assigned to another port (for security...)
- ✅ Ports can be "open", "filtered" (firewall), or "closed"
- 🍸 A port can, according to the protocol, receive TCP, UDP, or both TCP and UDP messages.
- 🔥 Port 0 is called wildcard port. When used by a program, it automatically be replaced by any available port.
Networking models
OSI model
The Open Systems Interconnection (OSI or ISO/OSI) model is a standardized representation of how we could send a message between two machines 🤝. It's made of 7 layers:
- Layer 7 - Application: programs are exchanging data
- Layer 6 - Presentation: standardize, encrypt, compress
- Layer 5 - Session: try to establish a connection
- Layer 4 - Transport: select a protocol
- Layer 3 - Network: create a packet
- Layer 2 - Data Link: resolve MAC
- Layer 1 - Physical: binary to signals
A computer generate a message at a layer. The message go down every layer until it's sent 📩. When a computer receives a message, it will go up every layer in reverse order 📖.
Each time a message go down, a header is added. This is called encapsulation 📥. When it goes up, it's called de-encapsulation 📤.
The Protocol Data Unit 📜 (PDU) is generated at each layer. It's both the layer protocol headers, and the previous PDU as the data, which is usually called payload.
TCP/IP model
The TCP/IP model was introduced before the OSI model, but remains the most used because it's more compact 🤏. It's made of 4 layers:
- Layer 4 - Application: Layers 5 to 7 of OSI
- Layer 3 - Transport: Layers 4 of OSI (socket, port...)
- Layer 2 - Internet: Layers 3 of OSI (IP, ETH...)
- Layer 1 - Physical: Layers 1, and 2 of OSI (Wi-Fi, ADsr, ETH...)
➡️ Some are splitting "Layer 1" back into two layers like in OSI, but it's not what's defined in the RFC1122 standard.
➡️ See also the model OSI/TCP/IP.
Protocols
A protocol is a set of instructions formalizing the way of communicating between devices (endianness, floating numbers format, charset, separators, integrity, errors...).
Each protocol can be represented using a Message Sequence Chart, describing how two machines are interacting using this protocol.
Layer 7: Application Layer (data) 🧑
| File transfer 📂 | |
| Mail transfer 📫 | |
| Remote shell access 🧑💻 | |
| Web requests 🌍 | |
| Remote desktop access 💻 | |
| Domain resolution 📍 | |
| Network file system 🗃️ | |
| IP addresses lease 🎯 | |
| Network Management 🧼 | |
| Others 🗃️ |
Layer 6: Presentation Layer (data) 🔒
Layer 5: Session Layer (data) 📶
Layer 4: Transport Layer (segment/datagram) 📫
Layer 3: Network Layer (packets) 🌍
Layer 2: Data Link Layer (frames) 🔢
Layer 1: Physical Layer (bits) 💺
- N/A
➡️ Note that some protocols may operate at multiple layers.
👻 To-do 👻
Stuff that I found, but never read/used yet.
- see SRM notes
- IPV6 EUI64 (texas)
- VIP (virtual IP?)
Certification
- 200-301 CCNA (goffinet)
Network segmentation
- VRFs (Virtual Routing and Forwarding)
Random
- Streaming network telemetry
- faidherbe
Traffic mirroring: See also NetFlow to collect and analyze network traffic data.
Network or protocol analyzers: Wireshark, tcpdump...
Triple-A model: Authentication, Authorization, and Accounting. It's a framework to control who can access the network, and what can they do. These are usually implemented by AAA-servers. See the RADIUS or the TACACS+ protocol...

