Wireshark
Wireshark is a well-known and popular GUI for packet analysis. When starting wireshark, select an interface to capture traffic. You can also load a saved capture (.pcap, .pcapng).
There is a CLI version called tshark and a TUI version called termshark.
If packets are encrypted, you need the private key. You can load it at: Edit > Preferences > Protocols > TLS > RSA Key list > +. Set the keyfile, while you might also set the server IP and port.
➡️ Protocols such as SSH, RDP, HTTPS, etc.
Wireshark Basic Overview
Wireshark interface after opening a capture/capturing packets:
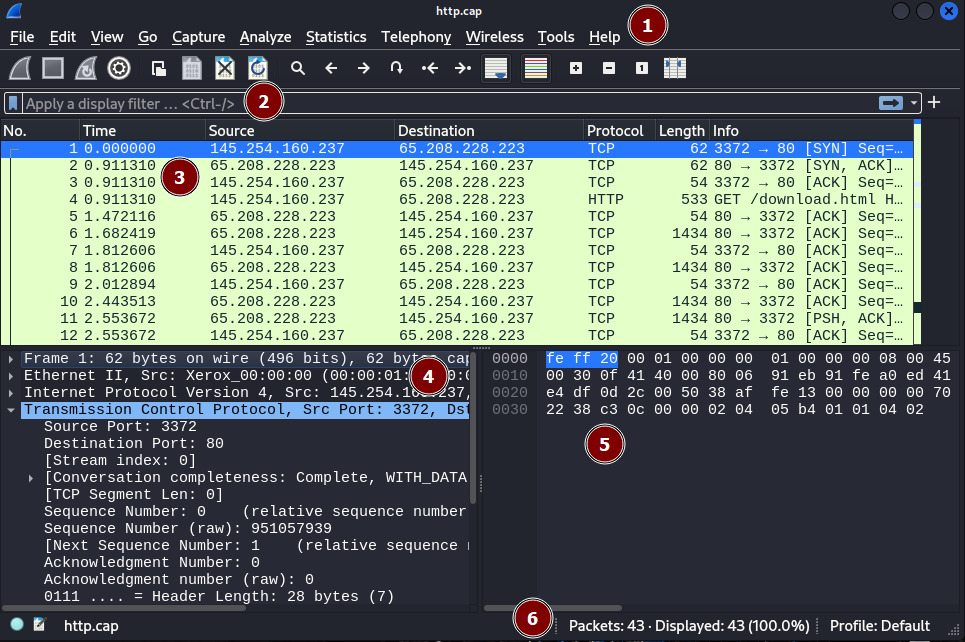
The GUI can be divided into the following sections:
-
Menu Bar 🌾: refer to useful menus
-
Display Filter 🥅: filters applied to the packet list
-
Packet List 🗃️: list of captured packets
-
Packet Details 📚: Double-click on a packet to see its details. They are divided in dropdowns for each OSI layer in the reverse order. Usually, the last dropdown is the one that you will want to inspect.
-
Packet Bytes 👽: nothing of interest?
-
Capture Summary ✍️: total number of packets
Common Features
Display Filter
To find interesting packets, you can apply filters on the packet list. Check out the bookmark icon to find saved filtering rules.
Additional insight on filtering rules:
ip.src == some_IP, orip.dest == some_IPip.addr == some_IPtcp.port == some_port, orudp.port == some_port- You also have options for each protocol, use autocompletion
- arp:
arp.opcode == 1... - http:
http.request.method == GET,http contains "User-Agent"... - ftp:
ftp.request.command(port 21) andftp-data(port 20) - ...
- arp:
- You can enter a protocol to only see this one (ex:
arp) - You can use operators such as
==, !=, >, <, ...and logical operators such as&&, ||, !. You can also use the text version:eq, ne, lt, gt, and, or, not.... Refer to the documentation + wiki.
Follow Stream
Right-click on a packet and select Follow > TCP Stream. This will apply the filter tcp.stream eq <stream_id> with a stream being a set of packets forming a conversation and open a window allowing us to easily view the message exchanged.
In the bottom right corner of the newly opened window, you can navigate through the streams using arrows.
Useful menus
- Download HTTP file: File > Export Objects > HTTP
- Replace MAC with hostname: View > Name Resolution > Resolve Physical Addresses
- Copy [...]: When inspecting a packet, right-click on a field, and go to "Copy" to copy the value/... Use CTRL+C for the whole line.
- Protocol stats: Statistics > Protocol Hierarchy
- Stats per IP: Statistics > Endpoints
👻 To-do 👻
Stuff that I found, but never read/used yet.

